The condition that occurs when a hash function maps two or more distinct search keys into the same location is called a(n) ______.
a) disturbance
b) collision
c) rotation
d) congestion
b.
Computer Science & Information Technology
You might also like to view...
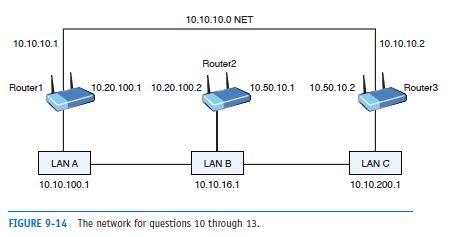
List two static routes to route data from LAN A to LAN C in the network shown in Figure 9-14, assuming the subnet mask 255.255.255.0.
Computer Science & Information Technology
The ________ passes the request to a central location
Fill in the blank(s) with correct word
Computer Science & Information Technology
TCP/IP uses a numeric value as an identifier to the applications and services on these systems.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The objective of the ________ control category is to avoid breaches of any law, statutory, regulatory, or contractual obligations, and of any security requirements.
A. access B. asset management C. compliance D. business continuity management
Computer Science & Information Technology