Data cannot be stolen directly from a computer on the Internet
Indicate whether the statement is true or false
FALSE
You might also like to view...
Assume the array nums has been filled as shown. What is the output of the following program segment?
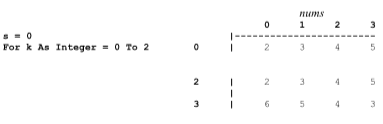
(A) 64
(B) 12
(C) 13
(D) 25
(E) None of the above
How is a graph characterized?
a. By the number of vertices and edges it has b. By the number of vertices it has c. By the number of edges it has d. By the product of its vertices and edges
The == symbol is referred to as the ______ operator.?
Fill in the blank(s) with the appropriate word(s).
?In a large IS organization, the professional who is responsible for maintaining the security and integrity of the organization's systems and data is__________.
A. ?the data center manager B. ?the data security manager C. ?the system security operator D. ?the information systems security analyst