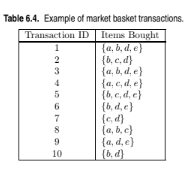
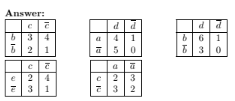
Draw a contingency table for each of the following rules using the trans- actions shown in Table 6.4.
.![]()
The original association rule mining formulation uses the support and confi-
dence measures to prune uninteresting rules
You might also like to view...
You have lots of images on your hard drive totaling 500 million bytes. A 2 Gigabyte storage device will be adequate to store those photos
Answer the following statement true (T) or false (F)
What’s wrong with this code? Find the error(s) in the following code, which is supposed to read a line from some- file.txt, convert the line to uppercase and then append it to somefile.txt.
string strPath = "somefile.txt"; string strContents; StreamWriter objStreamWriter; objStreamWriter = new StreamWriter( strPath, true ); StreamReader objStreamReader; objStreamReader = new StreamReader( strPath ); strContents = objStreamReader.ReadLine(); strContents = strContents.ToUpper(); objStreamWriter.Write( strContents ); objStreamReader.Close(); objStreamWriter.Close();
Which of the following is NOT an argument in the majority of database functions?
A) Field B) Dialog C) Criteria D) Database
You access the Adobe Application Manager dialog box, using which of the following?
A. Updates on the Help menu B. DPS Desktop Tools on the Help menu C. Updates on the Window menu D. DPS Desktop Tools on the Window menu