An application may rely on other files, in particular, ______________ files.
Fill in the blank(s) with the appropriate word(s).
DLL
correct
Computer Science & Information Technology
You might also like to view...
Which of the following is a value that is written into the code of a program?
a. a literal b. an assignment statement c. an operator d. a variable
Computer Science & Information Technology
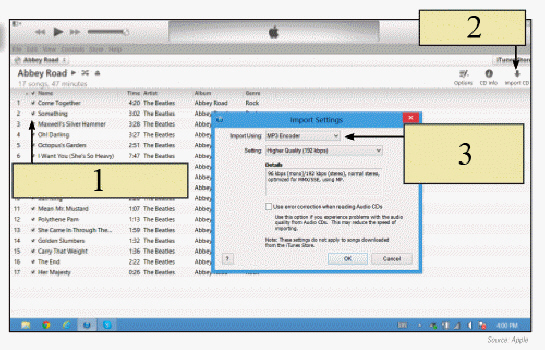 In the figure above, which of the following software is being used?
In the figure above, which of the following software is being used?
A. Windows Media Player B. Apple iTunes C. Apple iRip D. Windows Music Player
Computer Science & Information Technology
The ____ element is used to display prompting text on the screen.
A. prompting B. input C. legend D. label
Computer Science & Information Technology
When using the Common Internet File System (CIFS), which security model will require network users to have a user name and password to access a specific resource?
A. NT level security B. Share-level security C. User-level security D. CIF level security
Computer Science & Information Technology