Information security can begin as a grassroots effort in which systems administrators attempt to improve the security of their systems, often referred to as the bottom-up approach. _________________________
Answer the following statement true (T) or false (F)
True
You might also like to view...
In new project files, in a Gantt chart, the current date is represented by a ____ line.
A. solid red B. dashed blue C. solid horizontal D. gold vertical
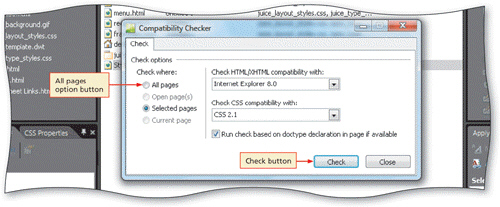 The Compatibility Checker dialog box, shown in the accompanying figure, is opened by clicking Compatibility Reports on the ____________________ menu.
The Compatibility Checker dialog box, shown in the accompanying figure, is opened by clicking Compatibility Reports on the ____________________ menu.
Fill in the blank(s) with the appropriate word(s).
____________________ is a list attached to an object in a system. It consists of control expressions, each of which grants or denies some ability to a particular user or group of users.
Fill in the blank(s) with the appropriate word(s).
Program control is best defined as:
a) specifying the degree of control a program has over the computer it is executed on b) specifying the line of code that is executing at a given time c) specifying the order in which the statements are executed d) None of the above.