The arc structure in the ADT implementation contains a pointer to the ____ and a pointer to the next arc in the path from the related vertex.
A. destination vertex
B. source vertex
C. head
D. next arc on the shortest path to the head
Answer: A
You might also like to view...
Which of the following buttons adds a slide to your presentation?
A. ![]()
B. ![]()
C. ![]()
D. ![]()
A company that transmits data over the telephone is con- cerned that its phones could be tapped. All its data is transmitted as four-digit int values. The company has asked you to write an application that encrypts its data so that the data may be transmitted more securely. Encryption is the process of transforming data for security reasons. Your application should read a four-digit integer input by the user in a JTextField and encrypt the information as described in the steps of this exercise when the user clicks the Encrypt JButton (Fig. 6.35).
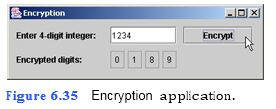
```
a) Copying the template to your working directory. Copy the C:Examples Tutorial06ExercisesEncryption directory to your C:SimplyJava directory.
b) Opening the template file. Open the Encryption.java file in your text editor.
c) Coding the Encrypt JButton’s ActionPerformed event handler. Add the code for Steps d through f to event handler encryptJButtonActionPerformed (lines 138–141).
d) Obtaining the user input. In line 140, insert a statement that obtains the user input from numberJTextField, converts it to an int and assigns the value to int variable number.
e) Extracting the digits from the user input. Use the programming techniques you used to solve Exercise 5.17 to insert statements that extract the digits from int variable number. Store the digits of number in the int variables digit1, digit2, digit3 and digit4, respectively.
f) Encrypt each digit and display the encrypted results. Replace each digit by perform- ing the calculation (the sum of that dig
In Word, it is possible to create your own custom tab
Indicate whether the statement is true or false
____ coordinates activities related to the Internet's naming system, such as IP address allocation and domain name management.
A. National Center for Supercomputing Applications (NCSA) B. Web Consortium (W3C) C. ICANN (Internet Corporation for Assigned Names and Numbers) D. Internet Society (ISOC)