Which of the following describes a firewall?
A) a malicious program that enters program code or destroys data without authorization
B) when two or more people cooperate together to defraud a company
C) a technique for protecting data
D) when a company defrauds its suppliers by making false claims
C
You might also like to view...
If delivery is to be made without moving the goods, title passes from the seller to the buyer at the time and place of contracting if the goods have been identified to the contract.
Answer the following statement true (T) or false (F)
Companies engaged in different types of profit-making activities are likely to be divided by
a. size; b. profits; c. time; d. departments; e. managers
List the tables with primary keys, attributes, and foreign keys that implement the following UML Class diagram given the accompanying list of attributes.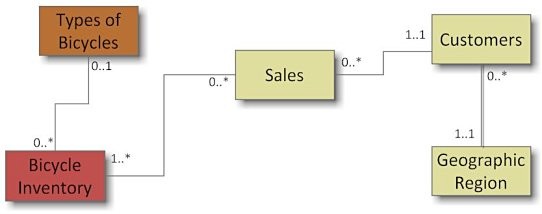 Attributes:Bicycle colorBicycle product numberBicycle quantity on handBicycle sizeBicycle TypeBicycle Type DescriptionCustomer addressCustomer nameCustomer numberGeographic region descriptionGeographic region identifierNumber of bicycles of this type on handPrice of this bicycle sold on this invoiceQua Quantity of this bicycle sold on this invoiceSale total $ amountSales invoice dateSales invoice numberYear-to-date sales $ for this region
Attributes:Bicycle colorBicycle product numberBicycle quantity on handBicycle sizeBicycle TypeBicycle Type DescriptionCustomer addressCustomer nameCustomer numberGeographic region descriptionGeographic region identifierNumber of bicycles of this type on handPrice of this bicycle sold on this invoiceQua Quantity of this bicycle sold on this invoiceSale total $ amountSales invoice dateSales invoice numberYear-to-date sales $ for this region
What will be an ideal response?
Generally, employees who earn less than _____ per week are automatically considered eligible for minimum wage and overtime as required by the Fair Labor Standards Act
a. $240 b. $300 c. $455 d. $550