What should you do if someone is looking over your shoulder as you log on to your computer?
A) Type your password quickly.
B) Ask them to leave the room.
C) Type your password at your normal pace so that you don't make a mistake, but tap your thumb a couple of times as if you are typing a key.
D) Wait until they are not looking to type your password.
D
You might also like to view...
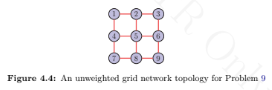
Consider an unweighted nine-node grid network, as shown in Figure 4.4. Write a program to add two LLs based on the MinAPL, MaxCC, and MaxCCD deterministic link addition strategies. Estimate the execution time of the three approaches. Also compare the APL obtained when using above mentioned LL addition techniques.
Which security layer verifies the identity of a user, service, or computer?
A. authentication B. repudiation C. physical security D. authorization
In the timescale, by default, the ____________________ scale is measured in weeks and displays the date for the Sunday of that week.
Fill in the blank(s) with the appropriate word(s).
The result of =ROUND(123.456,2 ) is ________
Fill in the blank(s) with correct word