What encryption is used with wireless networks?
A) Shared
B) WEP
C) VPN
D) SSID
Answer: B) WEP
You might also like to view...
a. Draw a time event diagram each to show the sequence of events and the blocking and unblocking of each process:
7. In a distributed system three processes P1, P2, P3 are engaged in interprocess communication. Suppose the following sequence of events occurred: At time 1, P3 issues a receive from P2. At time 2, P1 sends m1 to P2. At time 3, P2 issues a receive from P1. At time 4, P2 receives m1. At time 5, P2 sends message m1 to P3. At time 6, P3 receives m1; P1 issues receive from P2. At time 7, P2 issues a receive from P3. At time 8, P3 sends m2 to P2. At time 9, P2 receives m2. At time 10, P2 sends m2 to P1. At time 11, P1 recieves m2. i. on a communication system which provides blocking send operation and blocking receive operation. ii. on a communication system which provides nonnblocking send operation and blocking receive operation.
FIGURE EX 6-1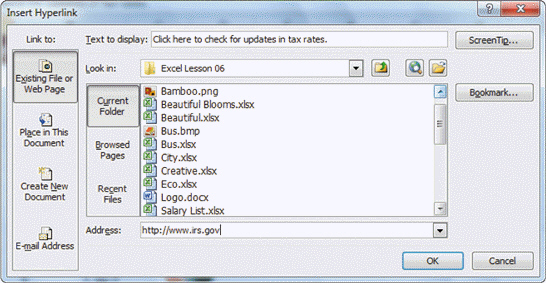 In order to access the Insert Hyperlink dialog box shown in Figure EX 6-1 above, you would ____.
In order to access the Insert Hyperlink dialog box shown in Figure EX 6-1 above, you would ____.
A. Click the cell she wants to use for the hyperlink. On the Insert tab of the Ribbon, in the Links group, click the Hyperlink button. B. Right-click the cell or object, and then click Hyperlink on the shortcut menu C. either a. or b. D. neither a. nor b.
A(n) ____________________ is a strip across the top of a window that contains one or more menu names.
Fill in the blank(s) with the appropriate word(s).
Lightning connector has 8-pins.
a. true b. false