Describe two common sources of security problems among end users.
What will be an ideal response?
Failure to take proper security precautions with passwords, anti-malware, and confidential information is one source. Another is vulnerability of end user to various scams and piracy.
You might also like to view...
Discuss the manner in which Java passes parameters to a method. Is this technique consistent between primitive types and objects? Explain.
What will be an ideal response?
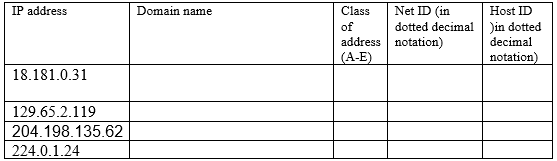
Complete the following table:
The __________ vulnerability assessment is a process designed to find and document selected vulnerabilities that are likely to be present on the organization's internal network.
A. intranet B. Internet C. LAN D. WAN
Briefly describe what happens after the source address table (SAT) is created in the switch.
What will be an ideal response?