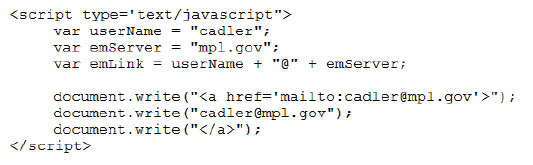
 In the figure above, what is the value stored in emLink?
In the figure above, what is the value stored in emLink?
A. cadler@mpl.gov
B. usernName@mpl.gov
C. userName@emServer
D. none of the above
Answer: A
You might also like to view...
Which one of the following is the general format for a variable declaration statement?
a. VariableName DataType; b. DataType VariableName; c. DataName VariableType; d. NameType VaraibleData;
_________ occurs when phishing emails are targeted to a specific individual and appear to come from an organization or person that the targeted individual has an association with. A. Spear phishing B. DNS phishing C. Individual phishing D. Associated phishing
Fill in the blank(s) with the appropriate word(s).
When working with video files, an Adobe Flash media file has a file extension of ________
A) .avi B) .mp3 C) .swf D) .asv
A(n) ____________________ is like a virus, but it can spread without human action across networks.
Fill in the blank(s) with the appropriate word(s).