Which of the following refers to an internal procedure by which authorized changes are made to software, hardware, network access privileges, or business processes?
A) Change control
B) NIST framework
C) Standard operating procedure
D) Patch management
A) Change control
Computer Science & Information Technology
You might also like to view...
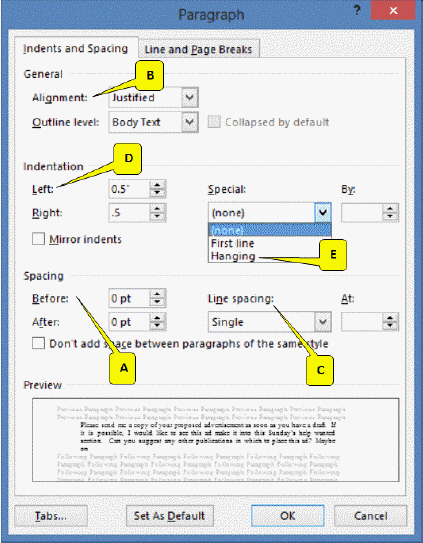 Refering to the accompanying figure, which callout points to the indent style that is used for numbered lists?
Refering to the accompanying figure, which callout points to the indent style that is used for numbered lists?
A. D B. E C. B D. C
Computer Science & Information Technology
Access will identify logical errors in calculated fields
Indicate whether the statement is true or false
Computer Science & Information Technology
Trace Contour, Wind, and Extrude are examples of ____ filters.
a. Distort b. Artistic c. Texture d. Stylize
Computer Science & Information Technology
A version of Microsoft Office to which you subscribe for an annual fee.
What will be an ideal response?
Computer Science & Information Technology