Port 443 usually refers to the ________ protocol
Fill in the blank(s) with the appropriate word(s).
Answer: HTTPS. Ports are extremely important for network forensics investigators because ports that are typically not used by a system can indicate a compromise.
Computer Science & Information Technology
You might also like to view...
The _______ qualifier is used to declare read-only variables.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
Which of the following is NOT required in order to view Web pages?
A. Internet connection B. computing device C. browser D. video player
Computer Science & Information Technology
A ________ window displays the contents of the current location
A) dialog B) navigation C) folder D) template
Computer Science & Information Technology
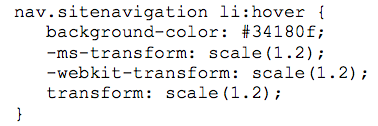
A. browser prefix B. class name C. pseudo-element D. pseudo-class
Computer Science & Information Technology