Consider the following B+-tree, where a node can contain two search key values and three pointers. Show the B+-tree after inserting a new record with search key value 38. (You must redraw the tree when giving the answer– leave the original tree intact.)
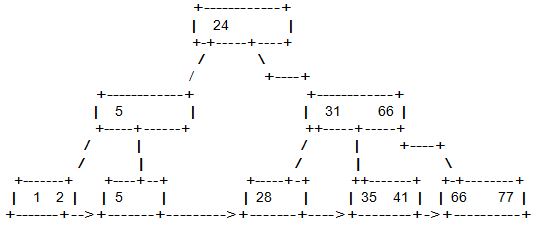
Solution:
The insertion will split the node 35,41, which will result in a split of the mid-level node 31,66 and filling up of the root node.
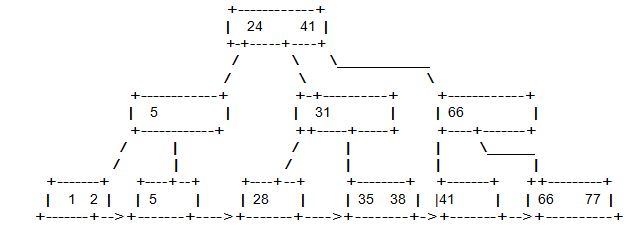
You might also like to view...
What is a constructor?
What will be an ideal response?
From the 1950s through the 1980s, almost all interactive dialogues between people and computers took place at the ____.
A. operating prompt B. command prompt C. operating line D. direction line
A potential weakness in an asset or its defensive control system(s) is known as a(n) __________.
A. threat B. attack C. exploit D. vulnerability
Which of the following cloud deployment models is also known as the internal or corporate cloud and is a cloud infrastructure operated by a single organization and implemented within a corporate firewall?
A. Community cloud B. Multi cloud C. Private cloud D. Public cloud