Emails that attempt to lure you to enter personal information are known as ________ emails
Fill in the blank(s) with correct word
phishing
Computer Science & Information Technology
You might also like to view...
What happens if a non-integer value is typed? What if the argument is omitted?
Write a program called twice that takes a single integer argument and doubles its value: $ twice 15 30 $ twice 0 0 $
Computer Science & Information Technology
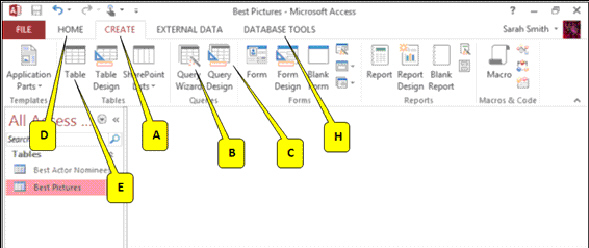 Referring to the accompanying figure, which callout points to the button you can click to create simple queries quickly?
Referring to the accompanying figure, which callout points to the button you can click to create simple queries quickly?
A. E B. B C. C D. H
Computer Science & Information Technology
Describe how to open a terminal window in the KDE and GNOME desktops environments.
What will be an ideal response?
Computer Science & Information Technology
A form is an example of a collection
Indicate whether the statement is true or false
Computer Science & Information Technology