What type of encryption algorithm uses two keys to encrypt and decrypt data?
A. signing
B. symmetric
C. asymmetric
D. hash
Answer: C
Computer Science & Information Technology
You might also like to view...
All of the following are examples of malware, EXCEPT ________
A) worms B) spam C) viruses D) spyware
Computer Science & Information Technology
Both statistical and logical inference can be identified by monitoring and analyzing unusual queries and by setting a baseline and threshold alert for unusual user activity.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The ________ tab will show you who is logged in to a computer
A) Login B) Users C) Personnel D) Account
Computer Science & Information Technology
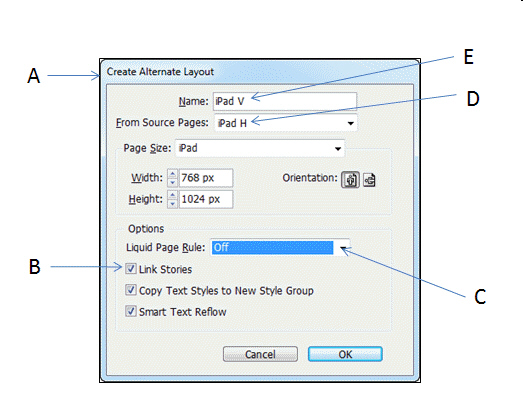 Item B in the accompanying figure is used to _______________ layers.
Item B in the accompanying figure is used to _______________ layers.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology