An intranet is a network based on Web technologies that allows selected outsiders, such as business partners and customers, to access authorized resources of a company's extranet.
Answer the following statement true (T) or false (F)
False
You might also like to view...
Answer the following statements true (T) or false (F)
1) C++ stores two dimensional arrays in row-major order. 2) This call explicitly signals a failure on the input stream instrm. instrm.setstate( ios::failbit ); 3) In order for two matrices to be conformable for multiplication, they must be of the same size. 4) Matrices A and B are conformable for multiplication if the number of columns in A is equal to the number of rows in B. 5) A multidimensional array declared mat[2][4][3] has 24 elements.
In open addressing hashing, where do we store all the items?
a. In the hash table itself b. Attached to the hash table using linked lists c. In secondary storage d. In an in-memory database
The get method appends the form data to the end of the URL specified in the action attribute.
Answer the following statement true (T) or false (F)
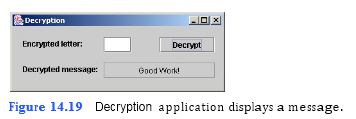
Develop an application that allows a user to decrypt a secret message (a string of numbers). The user should enter each number of the message one at a time in a JTextField. When the Decrypt JButton is clicked, the number should be decrypted to a letter. That letter should then be appended to the Decrypted message: JTextField. When the user enters the numbers 39, 79, 79, 68, 0, 55, 79, 82, 75, 1 in order, your application should appear as in Fig. 14.19.
a) Copying the template to your working directory. Copy the C:Exam- plesTutorial14ExercisesDecryption directory to your C:SimplyJava direc- tory.
b) Opening the template file. Open the Decryption.java file in your text editor.
c) Adding an instance variable. After the last GUI component is declared (line 18), add a declaration for a private String named message which will hold the decrypted message. Initialize message to the empty string. Use one line for a com- ment.
d) Storing the user input. Add code in the decryptJButtonActionPerformed method that will store the user input in an int variable named encryptedLetter. The rest of the code you will add in this exercises should be placed in the decryptJButtonAc- tionPerformed method.
e) Testing the user input. Your application should only accept user input in the range 0 to 94. Add an if statement that will test whether the user’s input is in the accepted range of values.
f) Decrypting the input. Add