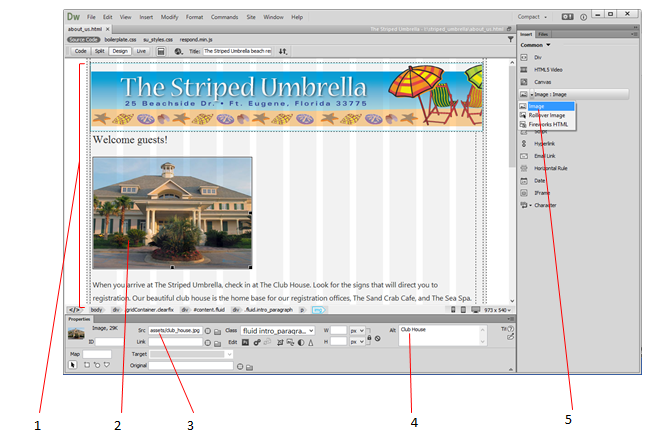
In the figure above, the number _____ points to the alt text box.
Fill in the blank(s) with the appropriate word(s).
Answer: 4
You might also like to view...
What are each of the following:
1. MIDI 2. MP3 3. Analog 4. Amplitude 5. Sampling rate
Which of the following is not confirmed by using a digital signature?
A) That the document has a valid password B) That the document was created by you C) That the document is valid D) That the document has not been changed
What is the purpose of standards?
A. To provide the steps necessary to achieve security B. To assess the security state C. To provide all the detailed actions that personnel are required to follow D. To provide recommended actions to carry out under certain conditions
The final process in the vulnerability assessment and remediation domain is the maintenance phase. __________
Answer the following statement true (T) or false (F)