As shown in the accompanying figure, if you point to a command on a menu that has an arrow to its right edge, a(n) ____ displays another list of commands.
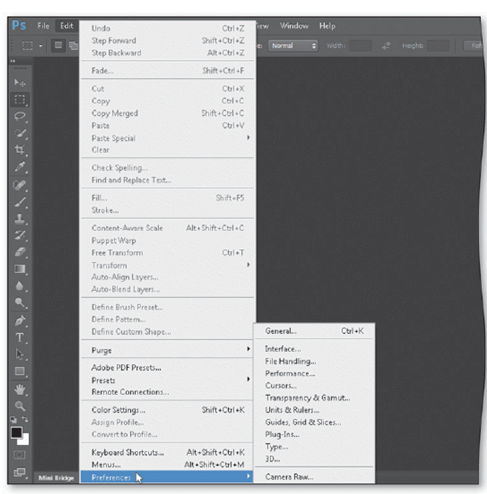
a. ellipsis
b. index
c. dock
d. submenu
d. submenu
Computer Science & Information Technology
You might also like to view...
The practice of writing a method to perform a single task and then calling that method whenever you need to perform that task is called:
a. Code reuse b. Divide and conquer c. Inheritance d. Parameter e. None of these
Computer Science & Information Technology
Which of the following would be considered a vulnerability?
A. installation of a firewall B. antivirus software C. Internet-connected computer D. spyware
Computer Science & Information Technology
Create a method that draws an X across the current picture using dashed lines.
What will be an ideal response?
Computer Science & Information Technology
The first phase in the development of the contingency planning process is the ____.
A. crisis plan B. disaster recovery plan C. incident response plan D. business impact analysis
Computer Science & Information Technology