Which of the following is NOT true when considering which fields to index?
A) Indexes can slow down searches and queries, but they can accelerate performance when you add or update data.
B) You cannot index a field whose data type is an OLE Object, Hyperlink, Memo, or Attachment.
C) You should index a field when the data is generally unique and when there are more different entries than duplicate entries.
D) You should index a field when you plan to frequently search or sort it.
A
You might also like to view...
Which of the following parts of a BDE event should be used for code that should execute once when the event first occurs?
a. Begin b. During c. End d. Start e. None of these
Modify the Security Panel application to use Java Speech API. The completed application is shown in Fig. 28.20.
a) Copying the template to your working directory. Copy the C:\Examples\ Tutorial28\Exercises\SecurityPanelEnhancement directory to your C:\Sim- plyJava directory. b) Opening the template file. Open the SecurityPanel.java file in your text editor. c) Importing Java Speech API packages. Import the javax.speech and the javax.speech.synthesis packages. d) Declaring instance variables. Above the SecurityPanel constructor, Declare an instance variable of type Synthesizer, which is used to speak text. e) Creating a Synthesizer object. Inside the SecurityPanel constructor, create a Synthesizer object, allocate the resource and get the synthesizer ready to speak. f) Adding code to the enterJButtonActionPerformed method. Find the enterJBut- tonActionPerformed method, which immediately follows nineJButtonActionPer- formed. Add code to the enterJButtonActionPerformed method to use the speech synthesizer. If the user enters a valid access code, the application should welcome the user and state the type of employee that the access code represents. If the access code is invalid, then the application should state that an invalid code was provided and that access is denied. g) Releasing the resources allocated to the speech synthesizer. Find the frameWindow- Closing method, which immediately follows enterJButtonActionPerformed. Inside the frameWindowClosing method, add code to release the resources allocated to the speech synthesizer. h) Saving the application. Save your modified source code file. i) Opening the Command Prompt window and changing directories. Open the Command Prompt window by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:\SimplyJava\Security- PanelEnhancement. j) Setting the CLASSPATH. Type SetClasspath.bat in the Command Prompt window to set the CLASSPATH environment variable. [Note: if your FreeTTS is installed in a directory other than C:\FreeTTS then replace C:\FreeTTS with your FreeTTS instal- lation directory in the SetClasspath.bat file.] k) Compiling the application. Compile your application by typing javac Securi- tyPanel.java. l) Running the completed application. When your application compiles correctly, run it by typing java SecurityPanel. Enter a correct access code, then click the # JBut- ton to verify that the application speaks the correct message. Try entering an incorrect access code. You should hear the application speak an error message notifying you that you did not enter a correct code. m)Closing the application. Close your running application by clicking its close button. n) Closing the Command Prompt window. Close the Command Prompt window by clicking its close button.
________ is a quick way to arrange open windows by dragging them to the edges of the computer screen
A) Zip B) Snip C) Snap D) Shake
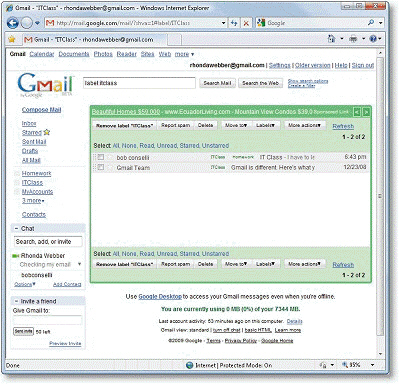 In the accompanying figure, "label:yourtag" in the search box will search for messages with that particular label.
In the accompanying figure, "label:yourtag" in the search box will search for messages with that particular label.
Answer the following statement true (T) or false (F)