What is the purpose of creating a "Security Operations Center"?
What will be an ideal response?
For large organizations that have sensitive or critical data, normal administrative expertise isn't enough to follow up and do damage assessment, risk remediation, and legal consultation. Large organizations need a permanent team whose members are responsible solely for security-response functions. Another function of a SOC is monitoring for artifacts left behind by attackers, which indicate that a system or network has been compromised.
You might also like to view...
The relation shown in Figure 15.12 describes hospitals (hospitalName) that require certain items (itemDescription), which are supplied by suppliers (supplierNo) to the hospitals (hospitalName). Furthermore, whenever a hospital (h) requires a certain item (i) and a supplier (s) supplies that item (i) and the supplier (s) already supplies at least one item to that hospital (h), then the supplier (s) will also be supplying the required item (i) to the hospital (h). In this example, assume that a description of an item (itemDescription) uniquely identifies each type of item.
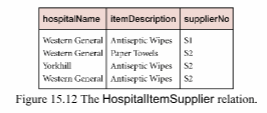
(a) Describe why the relation shown in Figure 15.12 is not in 5NF.
(b) Describe and illustrate the process of normalizing the relation shown in Figure 15.12 to 5NF.
Which Lasso tool is best for selecting areas of the canvas that are geometric in shape?
A. Lasso B. Magnetic Lasso C. Elliptical Lasso D. Polygonal Lasso
A social networking site is any site that enables individuals to connect and interact with other individuals.
Answer the following statement true (T) or false (F)
A mention in a SharePoint newsfeed post references another user through the use of the ________ symbol
A) @ B) & C) * D) #