Which of the following is likely to be accepted by a poorly designed application thereby leading to improper disclosure of data?
A. public key
B. asymmetric encryption
C. SHA1 hash
D. SQL injection
E. key escrow
Answer: D
You might also like to view...
What journal entry format is appropriate if sales returns and allowances occur on factored accounts?
A) Sales Returns and Allowances XXReceivable from Factor XX B) Receivable from Factor XXFactoring Expense XX C) Sales Returns and Allowances XXFactoring Expense XX D) Factoring Expense XX Sales Returns and Allowances XX
In the questions that follow, you will be asked to identify the blanks on the below diagram using the word bank: NADPH, NADP, ATP, ADP + P, carbon dioxide, oxygen, carbohydrate, water. Briefly explain the significance of each item.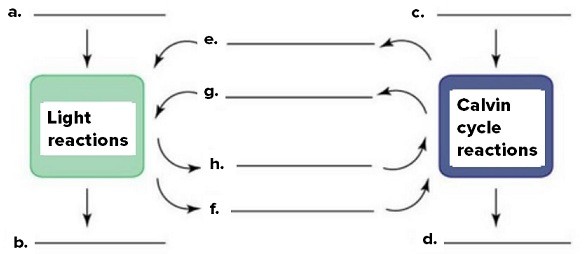 B is ________.
B is ________.
What will be an ideal response?
What is the probability that Jim will be accepted by at least one of the two universities?
Fill in the blank with correct word.
Agents and brokers facilitate transactions in exchange for commissions.
Answer the following statement true (T) or false (F)