A(n) ____________________ probe is the use of automated software to locate computers that are vulnerable to unauthorized access.
Fill in the blank(s) with the appropriate word(s).
port
Computer Science & Information Technology
You might also like to view...
Which of the following is false?
a. The three expressions in the for structure are optional. b. The initialization and increment expressions can be comma-separated lists. c. You must declare the control variable outside of the for loop. d. A for loop can always be used to replace a while loop, and vice versa.
Computer Science & Information Technology
Polymorphism enables you to:
a. program in the general. b. program in the specific. c. absorb attributes and behavior from previous classes. d. hide information from the user.
Computer Science & Information Technology
How would you define a fragment identifier at the top of a page, called “top”?
a. ```
```
b.
```
```
c.
```
```
d.
```
```
Computer Science & Information Technology
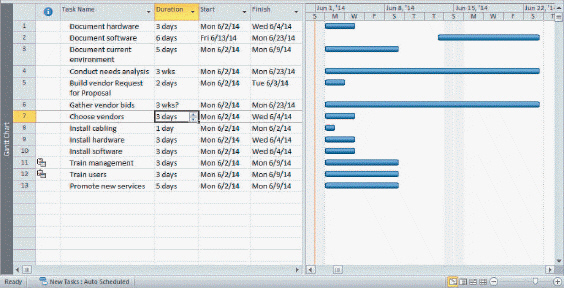 The item in row 7 of the Duration column is a(n) ____ duration.
The item in row 7 of the Duration column is a(n) ____ duration.
A. elapsed B. postponed C. eliminated D. estimated
Computer Science & Information Technology