Why is public key cryptography?
What will be an ideal response?
A completely different approach from symmetric cryptography is to use asymmetric cryptographic algorithms, also known as public key cryptography. Asymmetric encryption uses two keys instead of only one. These keys are mathematically related and are known as the public key and the private key. The public key is known to everyone and can be freely distributed, while the private key is known only to the individual to whom it belongs.
You might also like to view...
You can provide a parameterless constructor that contains code and takes no parameters, or that takes only Optional parameters so you can call it with no arguments.
a) Required b) Optional c) Voluntary d) Class
To add a JavaScript comment that is written on one line , you would begin the comment with ________
Fill in the blank(s) with correct word
FIGURE 9-2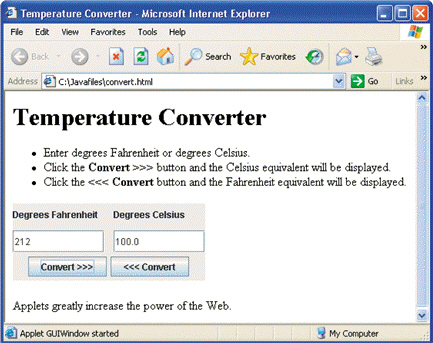 Figure 9-2 above shows an example of a(n) ____.
Figure 9-2 above shows an example of a(n) ____.
A. applet B. table C. inline image D. associative link
The determination of database requirements is part of a process known as ____________________.
Fill in the blank(s) with the appropriate word(s).