Preconfigured, predetermined attack patterns are called signatures. _________________________
Answer the following statement true (T) or false (F)
True
You might also like to view...
A hospital proposes to introduce a policy that any member of clinical staff (doctors or nurses) who takes or authorises actions that leads to a patient being injured will be subject to criminal charges. Explain why this is a bad idea, which is unlikely to improve patient safety and why it is likely to adversely effect the resilience of the organization.
What will be an ideal response?
Draw and label the lattice of consistent states (p1 state, p2 state), beginning with the initial state (0,0).
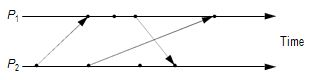
The figure above shows events occurring for each of two processes, p1 and p2. Arrows between processes denote message transmission.
If you do not see the four distinct zones of a PivotTable, you should click the Drop Zones icon in the Design tab of the Ribbon
Indicate whether the statement is true or false
A ________ is a series of characters
Fill in the blank(s) with correct word