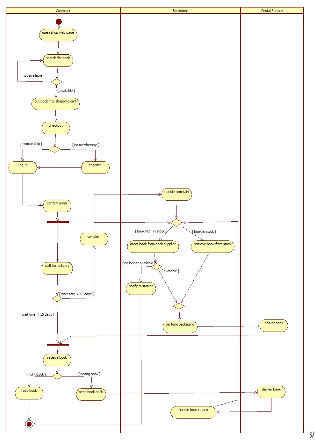
Consider the process of ordering a book via Internet. Draw an activity diagram representing each step of the process, from the moment you open the shop’s web page to the point when you start reading the book, including login or registration. Include activities that others need to perform.
Add additional exception handling to the activity diagram you have developed. Model the
following three exceptions:
1. The order got lost in the Internet
2. The wrong book is packaged
3. The ordered book is no longer available
You might also like to view...
Security principals can be either users or groups.
Answer the following statement true (T) or false (F)
________ programs allow you to experience a real situation through a virtual environment
Fill in the blank(s) with correct word
_______ is fast and is used as a memory cache, which speed overall computer performance by temporarily holding data and programming that the CPU may use in the near future.
Fill in the blank(s) with the appropriate word(s).
Filenames typically include a ____ at the end of the filename.
A. file extension B. file subscript C. file subname D. file attachment