Which of the following is a public key encryption algorithm?
a. IDEA
b. DES
c. Diffie-Hellman
d. AES
ANS: C
Computer Science & Information Technology
You might also like to view...
Use Figure 7-8 to answer questions below
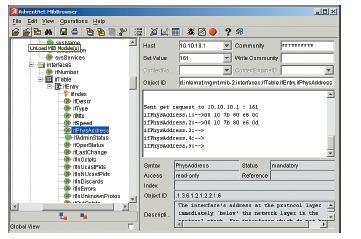
1. Which MIB is issued?
2. What information is returned?
3. Which port number is used?
4. Which protocol is being used? How do you know?
5. Who is the manufacturer of this networking device?
Computer Science & Information Technology
Traditionally, in the United States, the government relied upon the Travel Act of 1961 to prosecute online sports wagering and bookmaking activities
Indicate whether the statement is true or false.
Computer Science & Information Technology
To authenticate electronic documents as yours, you need to create a digital signature.?
Answer the following statement true (T) or false (F)
Computer Science & Information Technology
The ATM works on the principle of real-time processing.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology