SWAT is controlled by the ____ daemon.
A. BIND
B. sshd
C. tcpd
D. xinetd
Answer: D
You might also like to view...
For every program, Java defines an object named ____ through which textual values (letters, digits, punctuation, and so on) can be displayed on the screen.
A. System.monitor B. System.scanner C. System.out D. System.in
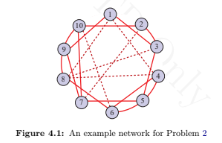
Consider the network shown in Figure 4.1. Write a program to calculate APL and ACC for the network. Among the categories of regular, small-world, and random networks, in what category does it belong?
The expression primes = (2, 3, 5, 7, 11) creates a list named primes.
Answer the following statement true (T) or false (F)
Which of the following security controls would be applied on individual hosts to monitor suspicious activities, by actively analyzing events occurring within that host, and blocking any suspicious or abnormal activity?
A. HIPS B. Spam filter C. HIDS D. Firewall