Packet analysis reveals multiple GET and POST requests from an internal host to a URL without any response from the server. Which of the following is the BEST explanation that describes this scenario?
A. Compromised system
B. Smurf attack
C. SQL injection attack
D. Man-in-the-middle
Answer: A. Compromised system
You might also like to view...
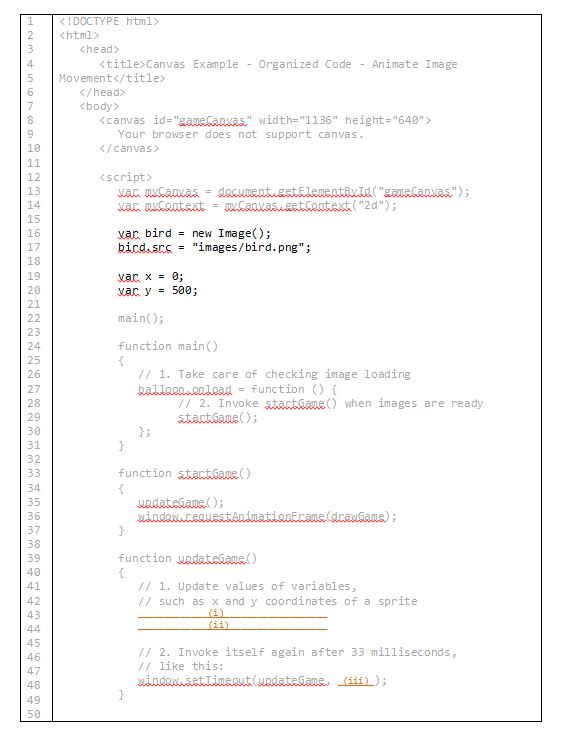
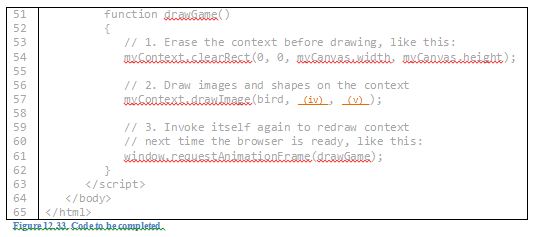
Complete the code in Figure 12.33. Suppose the image bird.png moves up 4 pixels and to the right 7 pixels every 33 milliseconds, i.e. about 30 times a second.
[This question is for UNIX/Linux users.] Create an output filter that performs word wrap- ping. If a line is longer than a certain number of characters, split the line over multiple lines. The num- ber of characters per line should be indicated in the command line. The program should read in keyboard input from the user, and format that input as specified, placing the result in file.txt.
Implement this using pipes and fork functions (child gets input from user, parent performs the fil- tering). What will be an ideal response?
On a form or a report, a(n) ________ box displays the data from a field in a table or query
Fill in the blank(s) with correct word
The cloning options control how the cloning tools sample the artwork.
Answer the following statement true (T) or false (F)