Which of the following attack types BEST describes a client-side attack that is used to manipulate an HTML iframe with JavaScript code via a web browser?
A. Buffer overflow
B. MITM
C. XSS
D. SQLi
Answer: C. XSS
You might also like to view...
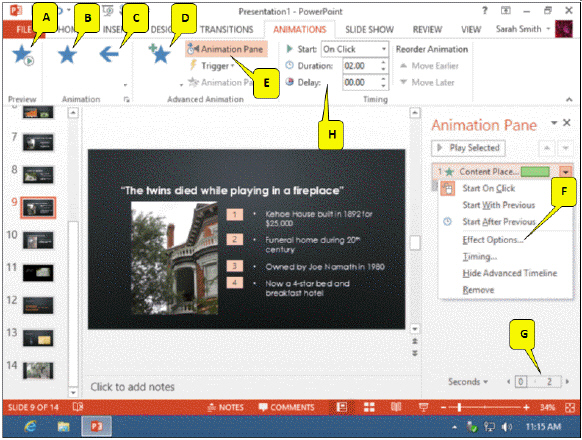 Referring to the figure above, which callout points to the Add Animation button to select an animation effect?
Referring to the figure above, which callout points to the Add Animation button to select an animation effect?
A. A B. B C. C D. D
____ employs resusable software components that can be run from within a variety of Windows programs.
A. Flash Player B. ActiveX C. SWF D. QuickTime
The Transport layer of the TCP/IP model uses both connection-oriented and connectionless protocols.
Answer the following statement true (T) or false (F)
Describe internal control procedures that would (1) prevent an employee from punching the time clock for another, absent employee and (2) prevent a supervisor from stealing the unclaimed paychecks of employees who have been terminated.
What will be an ideal response?