Consider the figure given below. When you request a network activity-such as printing a document using a network printer-the application program first passes the job to the _____.
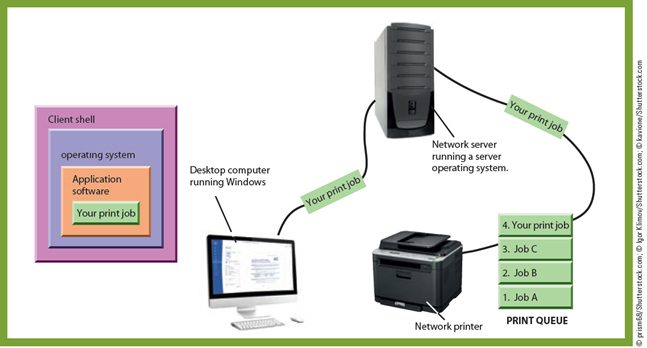
A. ?desktop operating system
B. ?network operating system
C. ?server operating system
D. ?embedded operating system
Answer: A
You might also like to view...
The sequence of commands for setting the enable secret to Chile is:
router> enable router# enable secret Chile True or False? Indicate whether the statement is true or false
Different ____________________ are used between layers of the OSI model to handle such things as error recovery and information routing between nodes.
Fill in the blank(s) with the appropriate word(s).
Standards, known as ____________________, have been created to make the Internet accessible to individuals with disabilities.
Fill in the blank(s) with the appropriate word(s).
You are using a gigabit Ethernet adapter (vmnic1) on an ESXi host, and you have found that the status screen displays the adapter as being connected at 100 Mb, full duplex. You have verified that the switch your server connects to has 1 Gbps capable ports. What is most likely the problem?
A. The adapter has been manually configured to a speed of 100 Mb, duplex operation. B. The adapter's driver in ESXi does not have 1 Gbps capability. C. The cable connecting the server and switch is damaged. D. The virtual machine using vmnic1 has limited the speed of the interface.