Training and awareness both help the organization to respond appropriately to security threats.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Use the _____ attribute on the form element to specify the name and location of the script that will process the form control values.
a. action b. process c. method d. none of the above
Which Cisco IOS command would be used to disable DTP negotiations on an interface?
A) switchport mode access B) switchport mode trunk C) switchport nonegotiate D) switchport trunk dtp disable
You can include multiple style declarations in an inline style by separating each one with a(n) ____.
A. question mark B. pair of braces C. colon D. semicolon
Give the coordinates of point G. ![]()
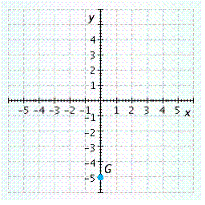 Determine the quadrant or axis where the point is located. Answer Quadrant I, Quadrant II, Quadrant III, Quadrant IV, origin, x-axis, or y-axis.__________
Determine the quadrant or axis where the point is located. Answer Quadrant I, Quadrant II, Quadrant III, Quadrant IV, origin, x-axis, or y-axis.__________
What will be an ideal response?