When Joshua sends a message to Larry, Joshua will use ________ to encrypt the message.
the public key
Joshua's public key
Larry's public key
Larry's private key
Larry's public key
You might also like to view...
The TryParse method parses the text, which means it looks at each character in the text, to determine whether the text can be converted to a number of the specified data type.
Answer the following statement true (T) or false (F)
The Windows app used for locating files and folders is
a. Disk Manager. b. Finder. c. File Explorer. d. Library Explorer.
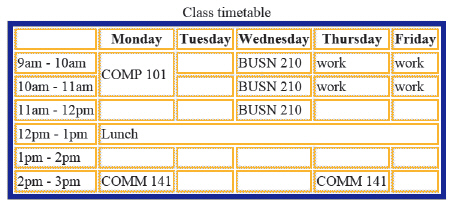 In the accompanying figure, the cell with the "COMP 101" contents is an example of the use of a ____ attribute.
In the accompanying figure, the cell with the "COMP 101" contents is an example of the use of a ____ attribute.
A. rowspan B. colspan C. merge D. spancol
All of the following statements are TRUE about finding relationships in data EXCEPT:
A) The covariance and correlation formulas are used to describe linear relationships between data. B) Covariance is a formula that can calculate the relationship between two variables, like age and dollars spent as well as the direction of the relationship. C) The correlation formula produces a value between –.1 and 1 that is called the correlation coefficient. D) The correlation coefficient is represented by the letter "r" in statistics and is a unitless value that describes the strength and direction of a relationship between two variables.