Define configuration rule policies and compare them to access control lists(ACLs).
What will be an ideal response?
Configuration rule policies are the specific instructions entered into a security system to regulate how it reacts to the data it receives. Rule-based policies are more specific to the operation of a system than access control lists(ACLs) are, and they may or may not deal with users directly. Many security systems - for example, firewalls, intrusion detection systems (IDSs), and proxy servers - use specific configuration rules to determine how the system handles each data element they process.
You might also like to view...
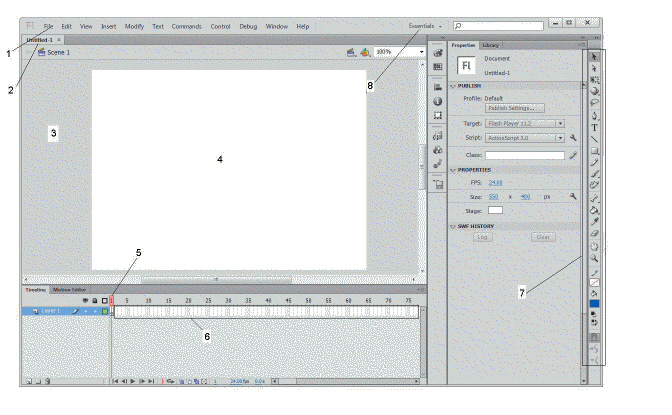 The item marked ____ in the accompanying figure is the Stage.
The item marked ____ in the accompanying figure is the Stage.
A. 2 B. 3 C. 4 D. 6
The processors that are found in just about all desktop and laptop computers are _____ compatible.
Fill in the blank(s) with the appropriate word(s).
?An attack that takes place before the security community and/or software developers become aware of and fix a security vulnerability is called the 'zero-day attack.'
Answer the following statement true (T) or false (F)
For templates that you create, you can instruct Word to display a content control's identifier, called the ____, by changing the properties of the content control.
A. Caption B. Tag C. Title D. Placeholder