Which of the following is a simple protocol that is used by applications that contain their own connection-oriented timeout values and retry counters, similar to those provided by TCP?
A. UDP
B. DoS
C. RTO
D. MSS
Answer: A
You might also like to view...
When you click and drag a file from the contents of the trash to a new location on your computer, the file is ____.
A. duplicated B. restored C. saved D. deleted
Which method of transmission divides the stream of information into small bits and maps them to a spreading code?
a. Direct-sequence spread spectrum b. Frequency-hopping spread spectrum c. Carrier sense multiple access with collision detection d. Carrier sense multiple access with collision avoidance
if (maxValue = 100) System.out.println ("Your limit has been reached"); ? Why is the above if statement illegal? How would you fix it?
What will be an ideal response?
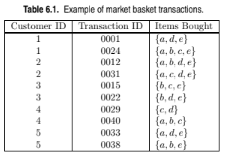
Suppose s1 and c1 are the support and confidence values of an associa- tion rule r when treating each transaction ID as a market basket. Also, let s2 and c2 be the support and confidence values of r when treating each customer ID as a market basket. Discuss whether there are any relationships between s1 and s2 or c1 and c2.
Consider the data set shown in Table 6.1