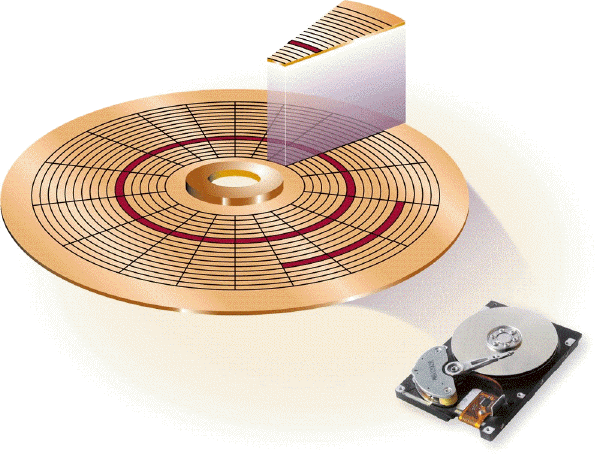
As shown in the accompanying figure, a(n) ____________________ is a narrow recording band that forms a full circle on the surface of the disk.
Fill in the blank(s) with the appropriate word(s).
track
You might also like to view...
The software application used to download and view Web pages is called a ____.
A. navigator B. browser C. viewer D. surfer
To combine the changes from multiple copies of a workbook into a single copy, you must add the ________ button to the Quick Access Toolbar
Fill in the blank(s) with the appropriate word(s).
The ____ constant instructs PHP to append data to any existing contents in a specified filename instead of overwriting it.
A. FILE_APPEND B. FILE_ADD C. FILE_INCLUDE D. APPEND_TO_FILE
A computer is suspected of being compromised by malware. The security analyst examines the computer and finds that a service called Telnet is running and connecting to an external website over port 443. This Telnet service was found by comparing the system's services to the list of standard services on the company's system image. This review process depends on:
A. MAC filtering. B. System hardening. C. Rogue machine detection. D. Baselining.