Which of these is the process of the system giving appropriate resource access to a user?
a. Authentication
b. Authorization
c. Logging in
d. Identification
B.
You might also like to view...
As shown in the accompanying figure, a hollow lock indicates that a layer is _____.
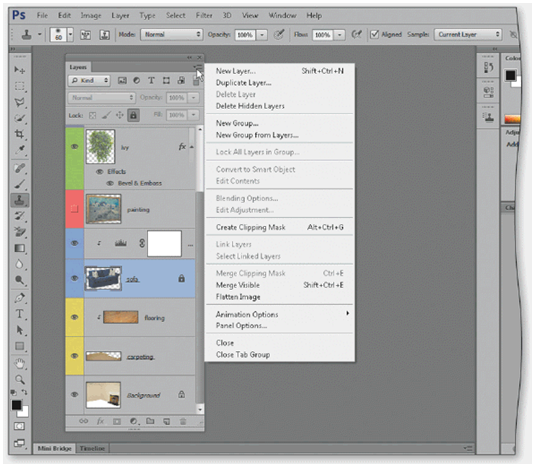
a. preset
b. transparent
c. fully locked
d. partially locked
The ________________ component displays a drop-down list from which the user can make a selection.
Fill in the blank(s) with the appropriate word(s).
Data validation is a ________
A) set of rules or constraints B) set of drop down options C) set of formatting codes D) set of masking characters
What should you do while copying data on a suspect's computer that is still live??
A. ?Open files to view contents. B. ?Make notes regarding everything you do. C. ?Conduct a Google search of unknown extensions using the computer. D. ?Check Facebook for additional suspects.