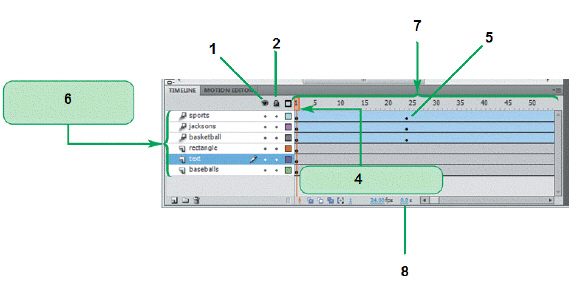
 The item marked ____ in the accompanying figure is the Lock/Unlock column.
The item marked ____ in the accompanying figure is the Lock/Unlock column.
A. 1
B. 2
C. 5
D. 8
Answer: B
Computer Science & Information Technology
You might also like to view...
The second time you switch to Reports view during a session, it opens to the ____ report you viewed.
A. last B. first C. largest D. smallest
Computer Science & Information Technology
Which of the following security settings can best help minimize brute force attacks on local user account passwords?
A. Logon time restrictions B. Screen lock timeout C. Audit logon failures D. Account lockout threshold
Computer Science & Information Technology
The spiral model of software development...
A. Includes project risks evaluation during each iteration. B. Is more chaotic than the incremental model. C. Ends with the delivery of the software product. D. All of these.
Computer Science & Information Technology
FreeTrip, MapQuest, and Expedia Maps are examples of online route planners.
Answer the following statement true (T) or false (F)
Computer Science & Information Technology