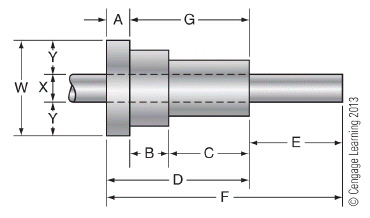
 To see the Link Checker options in Dreamweaver refer to item C in the accompanying figure.
To see the Link Checker options in Dreamweaver refer to item C in the accompanying figure.
Answer the following statement true (T) or false (F)
True
You might also like to view...
Which of the following is NOT among the common guidelines that should be reflected in the rule base to implement an organization's security policy?
A. only authenticated traffic can access the internal network B. employees can use instant-messaging only with external network users C. the public can access the company Web servers D. employees can have restricted Internet access
Using the ________ is an efficient way to locate a record in the table
A) Find Record button B) Locate button C) Find button D) Get Record button
________ is the destruction of hardware, software, or data.
A. Extortion B. Hacking C. Denial of Service D. Sabotage
You can change the zoom percentage using the ____________________ panel or the status bar by typing a new value in the Zoom text box.
Fill in the blank(s) with the appropriate word(s).