The most common technique for using an appropriate synchronization mechanism to serialize the accesses to prevent errors is to acquire a _______ on the shared file, ensuring that each process has appropriate access in turn.
A. lock B. code injection
C. chroot jail D. privilege escalation
A. lock
You might also like to view...
A __________________ traversal can be used to determine if a graph is connected.
a) inorder b) preorder c) depth-first d) breadth-first e) none of the above
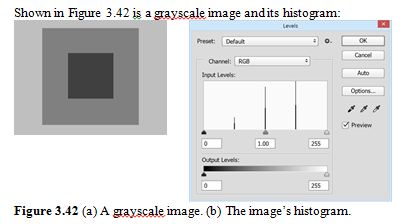
Match each of the bars in the histogram to the color it represents. (Draw arrows linking each bar and the color in the grayscale image in Figure 3.42.)
Prepare a diagram 0 DFD for New Century. Be sure to show numbered processes for handling appointment processing, payment and insurance processing, report processing, and records maintenance. Also, prepare lower-level DFDs for each numbered process. Sample DFDs follow:
What will be an ideal response?
________ enables administrators to customize the system’s access control policy using loadable kernel modules.
a) Linux security modules (LSMs) b) mandatory access control (MAC) c) pluggable authentication modules (PAMs) d) access control attributes