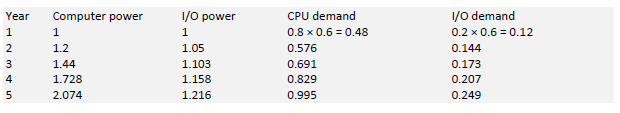
An application is 80% computation intensive and takes up 60% of a computer’s capacity (both CPU and I/O). Assume that this application will demand 20% more resources each year as it is updated; the computer’s processing power increases by 20% per year and the computer’s I/O performance increases by 5%. How will the situation develop over the next five years in terms of processing power and I/O usage?
What will be an ideal response?
You might also like to view...
Describe the purpose of the main steps in the physical design methodology presented in this chapter.
What will be an ideal response?
________ programs allow you to experience a real situation through a virtual environment
Fill in the blank(s) with correct word
Answer the following statements true (T) or false (F)
1) In a public-key algorithm, one key is used for both encryption and decryption. 2) Digital certificates are intended to be used indefinitely. 3) Secure Sockets Layer protects data stored on a merchant’s server. 4) Digital signatures can provide undeniable proof of the author of a document. 5) In a network of 10 users communicating using public-key cryptography, only 10 keys are needed in total.
In SharePoint, a(n) ________ list contains columns that enable you to manage specific information such as name, company, and phone numbers
Fill in the blank(s) with correct word