An attack in which the attacker attempts to impersonate the user by using his or her session token is known as:
A. Session replay
B. Session spoofing
C. Session hijacking
D. Session blocking
Answer: C
You might also like to view...
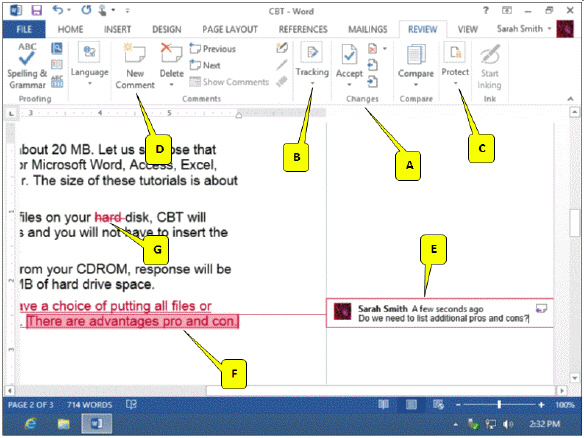 Refering to the accompanying figure, which of the following callouts points to the button that turns tracking on or off?
Refering to the accompanying figure, which of the following callouts points to the button that turns tracking on or off?
A. A B. B C. C D. D
What is the output of the following code segment?
``` for (k = 5; k > 0; k--) { for (i = 0; i < 5-k; i++) cout << '.'; for (j=0; j < 2*k-1; j++) cout << 'B'; cout << endl; } ```
PleaseRobMe was a website that used aggregation techniques to allow users to quickly find houses where the owners were away from their homes.
Answer the following statement true (T) or false (F)
Which malware attempts to embed itself deeply into a system in order to hide itself and other items, such as files, folders, or even executable processes?
A. Rootkit B. Trojan horse C. Worm D. Virus