Using tools in the accompanying figure, you can modify the ____, which is the spacing between a pair of characters.
a. kerning
b. tracking
c. bleeding
d. leading
A. kerning
You might also like to view...
Use debugging strategies that you have been using since grade school to check the math on this problem (* means multiplication)
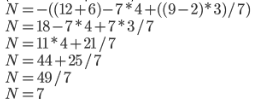
Authentication for WPA Personal is accomplished using a ____________ key.
Fill in the blank(s) with the appropriate word(s).
Answer the following statement(s) true (T) or false (F)
1. A data collector is a resource for storing data such as a spreadsheet while a data container is a mechanism to obtain data from a data source. 2. A risk score for a likelihood of 1 and an impact of 5 is 1/5. 3. An information security risk assessment project sponsor can be your immediate boss. 4. When the control has been implemented and data sheets about the control are available, we call the control a repeatable control of scale of 2. 5. A final impact score is the sum of the confidentiality, integrity and availability impact scores.
Why are employees sometimes not told that the company's computer systems are being monitored?
What will be an ideal response?