The AES key expansion algorithm takes as input a four-word (16-byte) key and produces a linear array of __________ words (176 bytes).
Fill in the blank(s) with the appropriate word(s).
44
You might also like to view...
To place an element in an ArrayList position for the first time, you usually use the method:
(a) put() (b) set() (c) add() (d) place()
____________________ management differs dramatically from incident response, as it focuses first and foremost on the people involved.
Fill in the blank(s) with the appropriate word(s).
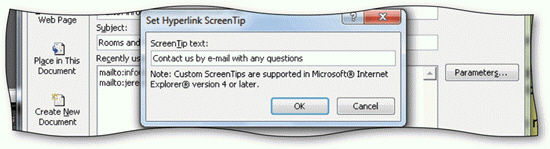 A ScreenTip added to a mailto link provides visitors with additional information, as shown in the accompanying figure.
A ScreenTip added to a mailto link provides visitors with additional information, as shown in the accompanying figure.
Answer the following statement true (T) or false (F)
Who is responsible for all circuits within their facility up to the designated demarcation point and provides troubleshooting assistance at the direction of the Global NetOps Support Center (GNSC)?
a. Communications focal point. b. Network control center. c. Node side coordinator. d. Circuit actions officer.