Methods are also called modules.
Answer the following statement true (T) or false (F)
True
Computer Science & Information Technology
You might also like to view...
__________ key encryption schemes are secure if the public key is authenticated.
A. Message B. Management C. Public D. Private
Computer Science & Information Technology
________ is a popular protocol used for retrieving e-mail messages
Fill in the blank(s) with correct word
Computer Science & Information Technology
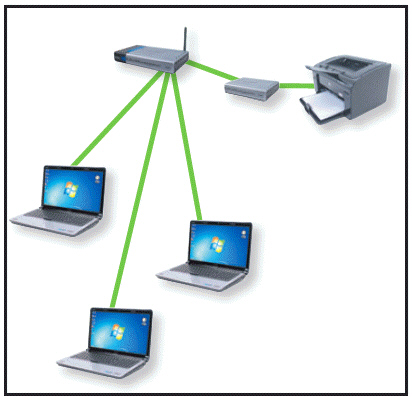 The accompanying figure shows the ____ method of connecting a printer to a network.
The accompanying figure shows the ____ method of connecting a printer to a network.
A. one-computer B. direct-to-router C. print-server D. direct-to-printer
Computer Science & Information Technology
A(n) ____________________ section defines an introduction to a document or section.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology