Use the function iter_swap to exchange the elements that are pointed to by two ________ iterators and exchanges the values in those elements.
Fill in the blank(s) with the appropriate word(s).
forward.
You might also like to view...
Which of the following is NOT true about securing a network?
A) There are both software firewalls and hardware firewalls. B) In a home network, the hardware firewall is established by protocols. C) In a network, the first layer of defense is the hardware at the access point to the network. D) A firewall prevents unauthorized access to a network.
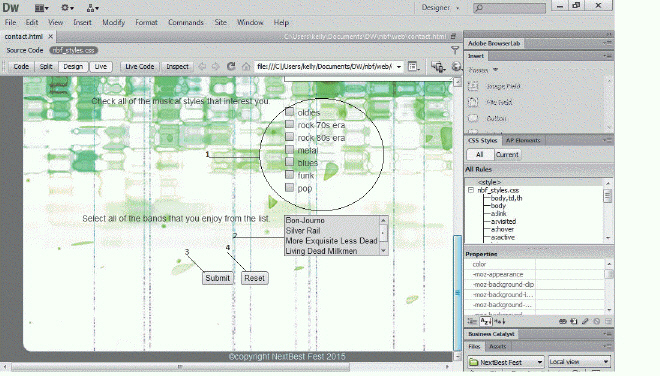 The item marked ____ in the accompanying figure accepts a height attribute that allows you to select how many rows are visible.
The item marked ____ in the accompanying figure accepts a height attribute that allows you to select how many rows are visible.
A. 1 B. 2 C. 3 D. 4
Which Component must be attached to a GameObject in order to play back an animation?
What will be an ideal response?
A security breach has been discovered, and you are responsible for performing the forensic investigation into the breach. What is the first step in this investigation?
A. Preservation B. Collection C. Examination D. Identification