____ is an encryption method that uses a public key and private key combination.
A. Symmetric key
B. Public key
C. Shared key
D. Universal key
Answer: B
You might also like to view...
COBIT is an acronym for which of the following?
A) Component Objectives for Information and Related Technologies B) Control Objectives for Information and Recovery Technologies C) Control Objectives for Information and Related Technologies D) Component Objectives for Information and Recovery Technologies
Analyze the DBMSs that you are currently using. What concurrency protocol does the DBMS use? What type of recovery mechanism is used? What support is provided for the advanced transaction
What will be an ideal response?
As opposed to ls, which lists the name of a file, the cat utility (Sobell, page 52) displays the contents of a file. Use the cat utility to display the con- tents of the file you just created.
What will be an ideal response?
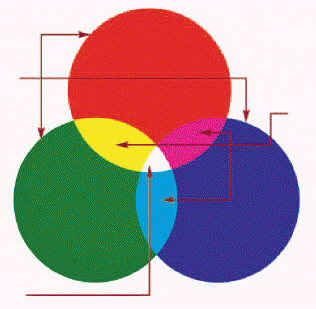 The additive color system, shown in the accompanying figure, is also referred to as the ____ color system.
The additive color system, shown in the accompanying figure, is also referred to as the ____ color system.
A. CYM B. RGB C. white light D. primary