A limitation in providing strong cryptography due to the tug of war between the available resources( time and energy) and the security provided by cryptography.
What will be an ideal response?
Resource vs. Security Constraint
Computer Science & Information Technology
You might also like to view...
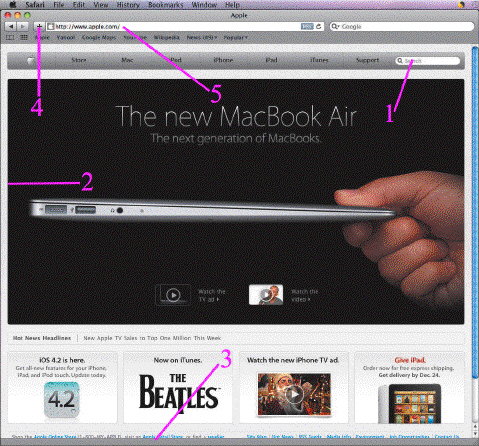 In the accompanying figure of a Safari window, Item 4 indicates the ____.
In the accompanying figure of a Safari window, Item 4 indicates the ____.
A. browser window B. Search field C. Add a bookmark button D. status bar
Computer Science & Information Technology
Good programming practice requires defining the number-of-items in the array as a(n) ____________________ before declaring the array.
Fill in the blank(s) with the appropriate word(s).
Computer Science & Information Technology
In sexting, an individual illegally shares a sexually explicit image, usually via MMS from a cell phone
Indicate whether the statement is true or false.
Computer Science & Information Technology
A point is _____ of an inch in height.
A. 1/72 B. 1/6 C. 1/5 D. 1/65
Computer Science & Information Technology