You determine which fields of information are displayed in the master page and which fields of information are displayed in the detail page when you set the parameters for the pages.
Answer the following statement true (T) or false (F)
True
You might also like to view...
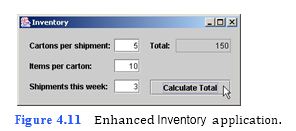
(Inventory Application Enhancement) Enhance the Inventory application to include a JTextField in which the user can enter the number of shipments received in a week (Fig. 4.11). Assume every shipment has the same number of cartons (each of which has the same number of items), and modify the code so that the Inventory application uses the num- ber of shipments in its calculation.
a) Copying the template to your working directory. Copy the C:Examples Tutorial04ExercisesInventory2Enhancement directory to your C:Simply- Java directory.
b) Opening the Command Prompt window and changing directories. Open the Com- mand Prompt window by selecting Start > Programs > Accessories > Command Prompt. Change to your working directory by typing cd C:SimplyJava Inventory2Enhancement.
c) Compiling the template application. Compile your application by typing javac Inventory.java.
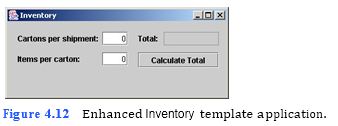
d) Running the template application. Run the enhanced Inventory template applica- tion by typing java Inventory. The GUI of the Address Book template application should appear as shown in Fig. 4.12. Note the differences from Fig. 4.11.
e) Opening the template file. Open the Inventory.java file in y
Since its launch in 2006, Twitter has become the number-two social media site preceded by LinkedIn
Indicate whether the statement is true or false
A business wants to start using social media to promote the company and to ensure that customers have a good experience with their products. Which security policies should the company have in place before implementation? (Choose two.)
A. All staff should be trained in the proper use of social media for the company. B. Specific staff must be dedicated to act as social media representatives of the company. C. Marketing professionals should write all senior staff blogs. D. Review the security policy to ensure that social media policy is properly implemented. E. IT staff should ensure that the company has sufficient bandwidth to allow for social media traffic.
Functions that do not have a return type are called ____ functions.
A. zero B. null C. void D. empty