Pete, the security engineer, would like to prevent wireless attacks on his network. Pete has implemented a security control to limit the connecting MAC addresses to a single port. Which of the following wireless attacks would this address?
A. Interference
B. Man-in-the-middle
C. ARP poisoning
D. Rogue access point
Answer: D. Rogue access point
You might also like to view...
To create a package, you must add a package statement at the ____________ of each class file.
a. beginning b. end c. before each method signature d. after the import statements
Which method is used to create a new item in a collection?
a. Store b. Insert c. Add d. Create
This type of boot occurs when the computer is already on and you restart it without turning off the power.
A. cold boot B. warm boot C. generic boot D. live boot
?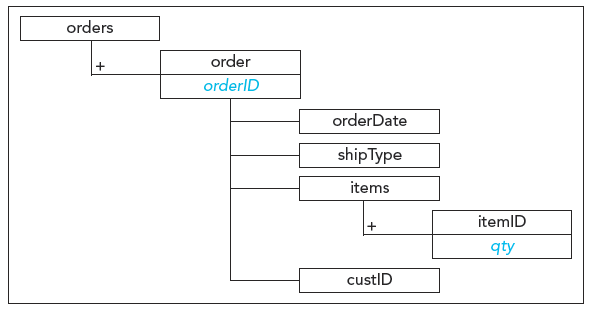
A. ?orderDate=preceding::order/orderDate B. ?not(orderDate=preceding::order/orderDate) C. ?orderDate=ancestor::order/orderDate D. ?not(orderDate=ancestor::order/orderDate)